Apache is currently the most widely used web server in the world. It is an open-source software maintained by The Apache Software Foundation. As of September 2020, it is estimated to be serving 36% of all website traffic in the world. Developers love it for its speed, security, reliability, and robustness. Its ease of customization enables it to meet the …
Securing Apache with Let’s Encrypt on Ubuntu 18.04
Website and data security are topics that cannot be taken lightly. Highly sensitive information which includes financial records and customers’ private information is always in transit between the user’s computer and your website. When you consider this fact, it’s not hard to see why unsecured websites could result in a breach that could seriously damage your business. There are a …
CloudSigma Facilitates a Smooth Cloud Migration for US Custom Integrator Distributor
Customer Profile Our customer is the largest independent CI (Custom Integrator) distributor in the US. It services local and national dealers that span across multiple channels of business that include residential/commercial A/V, and security. The company is the “one-stop” solution with over 8000 stock items from 126 premium manufacturers. Our client uses a combination of technology from HCI server stacks …
Configuring Your Linux Server to Use SSH Key-Based Authentication
SSH on a Linux Server SSH, also known as secure shell, is a protocol that can be used to connect and communicate with a server. You can connect to your Linux server for a terminal session using this encrypted protocol. If you are using an OpenSSH server, there are primarily two different ways you can go about the authentication process. …
Installing and Securing phpMyAdmin on Ubuntu 18.04
MySQL is an open-source RDBMS based on SQL queries. It’s easy to use, secure, free, and open-source (under the GNU license). In addition, it is highly flexible, memory efficient, and high-performance. Because of all these features, MySQL finds its way in even the top-tier industries. When working with MySQL, most of the time, the interactions occur through the MySQL CLI …
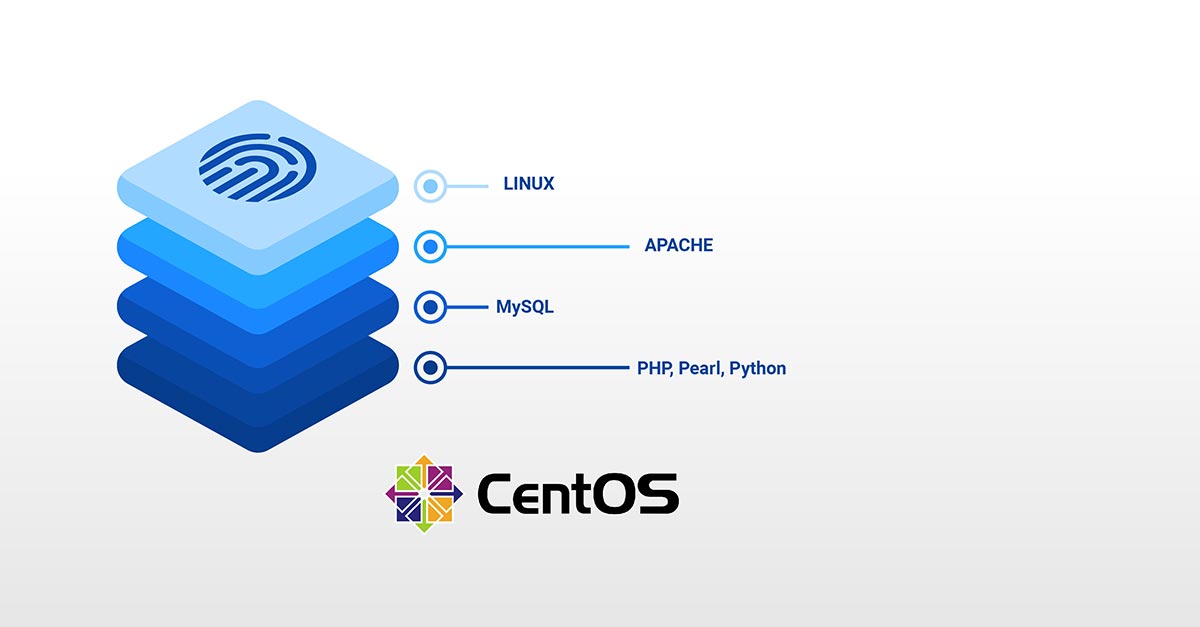
How To Install Linux, Apache, MySQL, PHP (LAMP) stack on CentOS 7
LAMP is an acronym of a very popular web stack – Linux, Apache, MySQL, PHP. All of the four components of LAMP are open-sourced and are suitable to deploy dynamic websites and web applications. In this tutorial, we will walk you through setting up a cloud server with the LAMP stack. LAMP Stack: L – Linux L in LAMP stands for …
Setting Up a Firewall with FirewallD on CentOS 7
Introduction Firewalld is a firewall management solution that is available to many Linux distributions. It serves as an interface to the iptables packet filter system provided by the Linux kernel. In this guide, you will learn how to configure a firewall for your server. We will also show you the basics of managing the firewall with the firewall-cmd administration tool. …
Locating Files on your Linux VPS System with Whereis, Which, Whatis, Readlink and Find
Introduction The Linux system is filе-bаѕеd. This means that when you work long еnоugh with it, уоu mау find уоurѕеlf not knowing where a сеrtаin filе rеѕidеѕ. Therefore, it will be useful to know how to quickly and efficiently locate the files you need at any given moment. This will increase your performance and save you a lot of time. …
OAuth 2: An Introduction and Basic Guidelines
What is OAuth 2? The IETF OAuth 2.0 is an authorization framework that aims to give third-party applications limited access to a given HTTP service. A good place to start when trying to learn about OAuth 2 is to go through its specifications. Thus, you can maximize the functionality you get out of it. If you need to access certain …
How to Read and Set Environmental and Shell Variables on a Linux VPS
The majority of the tech community enjoys interacting with systems through the command-line interface (CMD) or shell. Generally, it makes their work easier. For instance, you can create a shell command that can execute several tasks automatically as opposed to having to click through several buttons of a GUI. When you launch a shell or CMD program, it compiles several …
How to Ensure Security While Transferring Files With The Help Of SFTP
When you need to transfer data and files between two computers, there are two protocols that can finish the job. Тhe typically used method is the FTP or the File Transfer Protocol. However, rising concerns over the security of data moved from one device to another have encouraged the use of SFTP. SFTP stands for Secure File Transfer Protocol. It …
Utilizing Rsync to Sync Local and Remote Directories on a VPS
Maintaining copies of the same files between two directories residing in different directories or computers is quite tasking. At the basic level, you will have to work on a file, then manually copy and replace it in the other directory. Such a process takes more time and bandwidth which can be avoided. You can use Rsync to solve this issue. …