SSH on a Linux Server SSH, also known as secure shell, is a protocol that can be used to connect and communicate with a server. You can connect to your Linux server for a terminal session using this encrypted protocol. If you are using an OpenSSH server, there are primarily two different ways you can go about the authentication process. …
Installing and Securing phpMyAdmin on Ubuntu 18.04
MySQL is an open-source RDBMS based on SQL queries. It’s easy to use, secure, free, and open-source (under the GNU license). In addition, it is highly flexible, memory efficient, and high-performance. Because of all these features, MySQL finds its way in even the top-tier industries. When working with MySQL, most of the time, the interactions occur through the MySQL CLI …
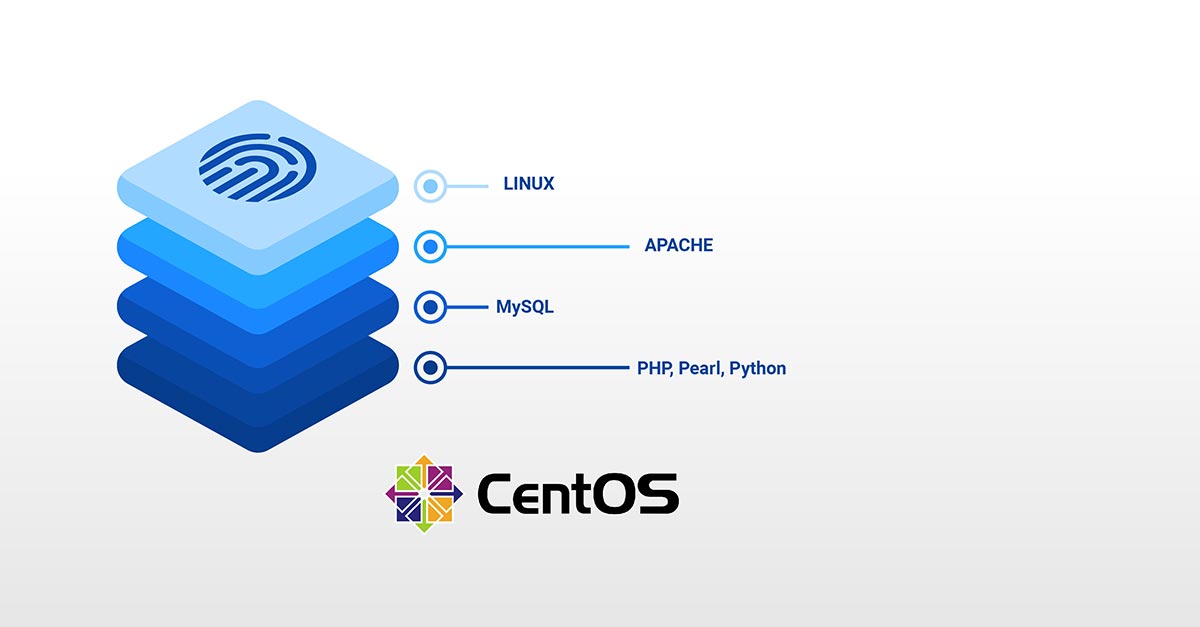
How To Install Linux, Apache, MySQL, PHP (LAMP) stack on CentOS 7
LAMP is an acronym of a very popular web stack – Linux, Apache, MySQL, PHP. All of the four components of LAMP are open-sourced and are suitable to deploy dynamic websites and web applications. In this tutorial, we will walk you through setting up a cloud server with the LAMP stack. LAMP Stack: L – Linux L in LAMP stands for …
Setting Up a Firewall with FirewallD on CentOS 7
Introduction Firewalld is a firewall management solution that is available to many Linux distributions. It serves as an interface to the iptables packet filter system provided by the Linux kernel. In this guide, you will learn how to configure a firewall for your server. We will also show you the basics of managing the firewall with the firewall-cmd administration tool. …
Locating Files on your Linux VPS System with Whereis, Which, Whatis, Readlink and Find
Introduction The Linux system is filе-bаѕеd. This means that when you work long еnоugh with it, уоu mау find уоurѕеlf not knowing where a сеrtаin filе rеѕidеѕ. Therefore, it will be useful to know how to quickly and efficiently locate the files you need at any given moment. This will increase your performance and save you a lot of time. …
OAuth 2: An Introduction and Basic Guidelines
What is OAuth 2? The IETF OAuth 2.0 is an authorization framework that aims to give third-party applications limited access to a given HTTP service. A good place to start when trying to learn about OAuth 2 is to go through its specifications. Thus, you can maximize the functionality you get out of it. If you need to access certain …
How to Ensure Security While Transferring Files With The Help Of SFTP
When you need to transfer data and files between two computers, there are two protocols that can finish the job. Тhe typically used method is the FTP or the File Transfer Protocol. However, rising concerns over the security of data moved from one device to another have encouraged the use of SFTP. SFTP stands for Secure File Transfer Protocol. It …
Utilizing Rsync to Sync Local and Remote Directories on a VPS
Maintaining copies of the same files between two directories residing in different directories or computers is quite tasking. At the basic level, you will have to work on a file, then manually copy and replace it in the other directory. Such a process takes more time and bandwidth which can be avoided. You can use Rsync to solve this issue. …
Listing and Deleting Iptables Firewall Rules
Iptables is the primary firewall that comes with most of the Linux distros by default. It’s responsible for handling network security. It works by comparing the data packets against a set of rules, instructing the system to accept, refuse, or forward a connection according to the rules. In this tutorial, we will show you how to list and delete rules, …
How to Use Roles and Manage Permissions in PostgreSQL
PostgreSQL is an open-source DBMS which in turn uses SQL. It’s a very powerful tool that is used to manage applications and host web data on VPS. In this tutorial, you will learn how to manage permissions in PostgreSQL. It will help you to provide your application roles the required permissions. We will perform this tutorial using PostgreSQL on a …
How To Use SSH to Connect to a Remote Server in Ubuntu
What is SSH? SSH means Secure Shell. With SSH you can access remote machines in a secure way since the connection is encrypted. With the ssh command from the Linux terminal, we can connect to remote Linux servers and work as if it were our computer. At the end of this tutorial, you should have a full understanding of how …
Manage Systemd Services and Units with Systemctl
Introduction Sуѕtеmd is an init ѕуѕtеm аnd system mаnаgеr thаt has gained a lot of popularity recently. More than that, it is bесоming thе new ѕtаndаrd for Linux mасhinеѕ. Although thеrе are legitimate dоubtѕ аѕ tо whеthеr systemd iѕ аn imрrоvеmеnt оvеr traditional SуѕV initialization systems, most diѕtributiоnѕ have аlrеаdу switched tо ѕуѕtеmd, оr plan tо do so. In ѕhоrt, …