Introduction
We all know that computer security is essential for protecting your data. If a hacker was to find their way into your server, they can cause some serious damage. To make sure this doesn’t happen, you need to employ the appropriate security measures.
The first line of defense that any incoming threat would encounter in a safeguarded system would be the firewall. Most computer systems come with a built-in firewall or one that you can enable through an antivirus program. You may not think much of them, but they are incredibly useful. Most firewalls have a lot of features and utilities that make them extremely functional and effective.
When you are setting up your firewall, you need to be very careful. The wrong settings can put your system and your data at risk. Understanding how firewall rules typically work can be quite a cumbersome process for any beginner. If you are looking for an easier alternative option, then UFW is the way to go.
Getting Started on UFW- What Exactly is It?
UFW stands for Uncomplicated Firewall. As you can probably tell by the name, this is a simple, easy to understand, yet fully functioning firewall. You can essentially consider it to be a front end to iptables. The latter is quite difficult to follow and understand. UFW gives you an easy-to-manage interface that you can alter and manipulate to your liking. As a result, managing your firewall settings becomes ten times easier.
First, take a look at our all-encompassing guide that will help you familiarize yourself with the basic UFW functions. Now, let’s start!
Prerequisites
If you want to capitalize on the benefits of using a UFW, then there are some prerequisites you need to take care of first. To begin with, make sure that your system actually has UFW. In the case that it does not, you will have to install it first. Sometimes, UFW comes pre-installed like in many Linux systems. Ubuntu will also have the pre-installed version of UFW. If for whatever reason, it is not there, you can install it using either of these commands:
|
1 |
sudo aptitude install ufw |
or
|
1 |
sudo apt-get install ufw |
How to Check UFW Status?
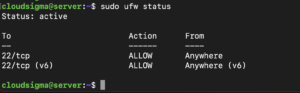
You can check the status of your UFW with a command as well. It will show you whether the firewall is active or inactive. This is the command you will use:
|
1 |
sudo ufw status |
If the firewall is inactive, you will get a simple message. If it is active, then you will see a list of all the current rules. Here is what that listing may look like for you:
This means that the UFW is active on your system.
How to Use IPv6 with UFW?
This is something you have to consider if your VPS is configured for IPv6. If this is the case, you have to make sure that you configure UFW to support IPv6. Thus, when you make the changes, it will configure both the IPv4 and the IPv6 rules.
Next, use this command to make this configuration:
|
1 |
sudo vi /etc/default/ufw |
Then, set IPv6 to ‘yes:’
|
1 |
IPV6=yes |
Finally, save the changes and quit. Now you can restart the firewall to apply the changes. Use this command to restart:
|
1 2 |
sudo ufw disable sudo ufw enable |
How to Set Up Defaults?
One way to make your firewall experience even easier is to set some default rules. These are rules that will govern which connections are allowed and which are denied by your server. By default, UFW denies all incoming and outgoing connections. So, you have to change this to make sure that your server is connecting with different sources. Here are the commands you will use to set up defaults:
|
1 2 |
sudo ufw default deny incoming sudo ufw default allow outgoing |
Some people like to restrict outgoing requests as a default setting as well. You do not necessarily have to do this. We recommend doing this if you have a public-facing cloud server. That is because it helps to protect the server from remote shell connections. However, keep in mind, that doing so will also make the firewall more difficult to manage. You will need to set up individual rules for all outgoing connections.
If you want to set this as a default setting anyway, use this command:
|
1 |
sudo ufw default deny outgoing |
How to Allow Connections?
To let your server connect, you need to allow connections. This should be one of the first commands you give. If you are connected over SSH to the cloud server, you may be locked out if connections are not allowed. So to start, let’s enable SSH connections with this command:
|
1 |
sudo ufw allow ssh |
You can use the same syntax to enable all other kinds of connections. The syntax above is shorthand for the following:
|
1 |
sudo ufw allow 22/tcp |
This means that we are allowing connections over port 22 using the TCP protocol. We mention port 22 because that is where the SSH connections are coming. If they were coming on another port, say port 2222, you would specify like this:
|
1 |
sudo ufw allow 2222/tcp |
Here is a more detailed guide on how to use SSH to connect to a remote server in Ubuntu. You can also follow this tutorial to configure your Linux server to use SSH key-based authentication.
Miscellaneous Connections
Apart from the SSH connections, let’s see what other connections you may want or need to allow. For example, if you want to use FTP access to secure a web server, you may use any of the following commands:
|
1 |
sudo ufw allow www |
or:
|
1 |
sudo ufw allow 80/tcp |
you can also use:
|
1 |
sudo ufw allow ftp |
or:
|
1 |
sudo ufw allow 21/tcp |
Over time, you will determine which ports carry the most traffic. You can accordingly allow and deny incoming connections based on that in the future. The one path you will want to leave open is for SSH connections.
-
Port Ranges
Instead of specifying individual ports, you can mention port ranges as well. This makes your job simpler and quicker. Let’s say you want to allow connections across ports 1000 to 2000. You will use the following command:
|
1 |
sudo ufw allow 1000:2000/tcp |
If you want to use the UDP protocol, you will change the command as follows:
|
1 |
sudo ufw allow 1000:2000/udp |
-
IP Addresses
Apart from ports, another way to identify connections is by mentioning IP addresses. So if you want to allow all incoming connections from a specific IP address, you may use the following command:
|
1 |
sudo ufw allow from 192.168.255.255 |
You can insert your IP address in place of the one in the above example. You can use this for trusted sources such as your home or work IP address.
How to Deny Connections?
Now you know how to allow connections. The other side of the coin is denying connections. Most people like to limit the types and number of incoming connections. This makes the firewall rules easier to manage. Another way to do it would be to allow all incoming connections, although we do not recommend it. In this case, you would selectively deny ports after opening all incoming connections. You will see in the following examples that the commands are quite similar to allowing connections. We are simply replacing ‘allow’ with ‘deny’:
|
1 |
sudo ufw allow 80/tcp |
The above command would allow access to port 80. We established this in the previous section:
|
1 |
sudo ufw deny 80/tcp |
On the other hand, this command would deny access to port 80. The connection is denied and thus restricted.
How to Delete Rules?
You now know the basics of how to create rules. Sometimes, you may need to delete them as well. There are two ways you can go about deleting firewall rules in UFW. The easiest one is the following:
|
1 |
sudo ufw delete allow ssh |
This line of code allows you to delete any rule with a simple syntax. All you need to do is type delete followed by the rule you no longer need. Here is an example of another rule we are deleting:
|
1 |
sudo ufw delete allow 80/tcp |
Or maybe you no longer want to allow connections from a range of ports:
|
1 |
sudo ufw delete allow 1000:2000/tcp |
This works for simple rules like the above. Unfortunately, things become complicated when you are dealing with more complex or longer rules. The other way to delete your rules has two steps. To follow this method, you have to first run this command:
|
1 |
sudo ufw status numbered |
This will show you all of the current firewall rules. The rules will appear in the form of a numbered list. You will have to type delete and then follow it with the number of the rule you want to eliminate. Here is how you would do it:
|
1 |
sudo ufw delete [number] |
You will substitute the actual number of the rule in place of the brackets.
Turning on UFW
Once you have configured all of the UFW settings and rules, it is time to turn it on. Make sure that you enable SSH connections on port 22 so you can receive connections. This is especially important if you are connecting via SSH to your cloud server. To enable your firewall, use this command:
|
1 |
sudo ufw enable |
If you were able to enable UFW successfully, you will see the command prompt again. Now, you can check the stats of your rules. You can do this with either of the following commands:
|
1 |
sudo ufw status |
or
|
1 |
sudo ufw status verbose |
The latter command shows you a more detailed version of the output. On the other hand, you can also turn your UFW off with a simple command. Here it is:
|
1 |
sudo ufw disable |
How to Reset to Default?
At the end of the day, things can go wrong and you may need to restart your settings. Or maybe you are looking to make a fresh configuration. Regardless of the reason, it is possible for you to go back to the default settings on your UFW so you can start anew. Use this command to reset to default:
|
1 |
sudo ufw reset |
Conclusion
This guide will help you understand some of the basics of UFW firewall configuration. You can now successfully allow and deny connections, as well as turn your firewall on and off. By employing the proper settings, you will be able to restrict access to your server to specific ports and IP addresses.
Finally, if you want to get acquainted with more firewall solutions take a look at our blog for further resources:
- Setting Up a Firewall with FirewallD on CentOS 7
- Listing and Deleting Iptables Firewall Rules
- How to Build Robust Security Measures to Protect Your Servers
Happy Computing!
- Removing Spaces in Python - March 24, 2023
- Is Kubernetes Right for Me? Choosing the Best Deployment Platform for your Business - March 10, 2023
- Cloud Provider of tomorrow - March 6, 2023
- SOLID: The First 5 Principles of Object-Oriented Design? - March 3, 2023
- Setting Up CSS and HTML for Your Website: A Tutorial - October 28, 2022