Iptables is the primary firewall that comes with most of the Linux distros by default. It’s responsible for handling network security. It works by comparing the data packets against a set of rules, instructing the system to accept, refuse, or forward a connection according to the rules. In this tutorial, we will show you how to list and delete rules, …
How to Use Roles and Manage Permissions in PostgreSQL
PostgreSQL is an open-source DBMS which in turn uses SQL. It’s a very powerful tool that is used to manage applications and host web data on VPS. In this tutorial, you will learn how to manage permissions in PostgreSQL. It will help you to provide your application roles the required permissions. We will perform this tutorial using PostgreSQL on a …
Clean Up Docker Resources – Images, Containers, and Volumes
Docker is one of the most popular products in organizations these days. It makes the process of managing applications in containers very easy. Docker provides portability, performance, agility, scalability, and isolation to the applications since it uses containers. Containers are more portable and require fewer resources than virtual machines. As you work with Docker, you tend to accumulate an excessive …
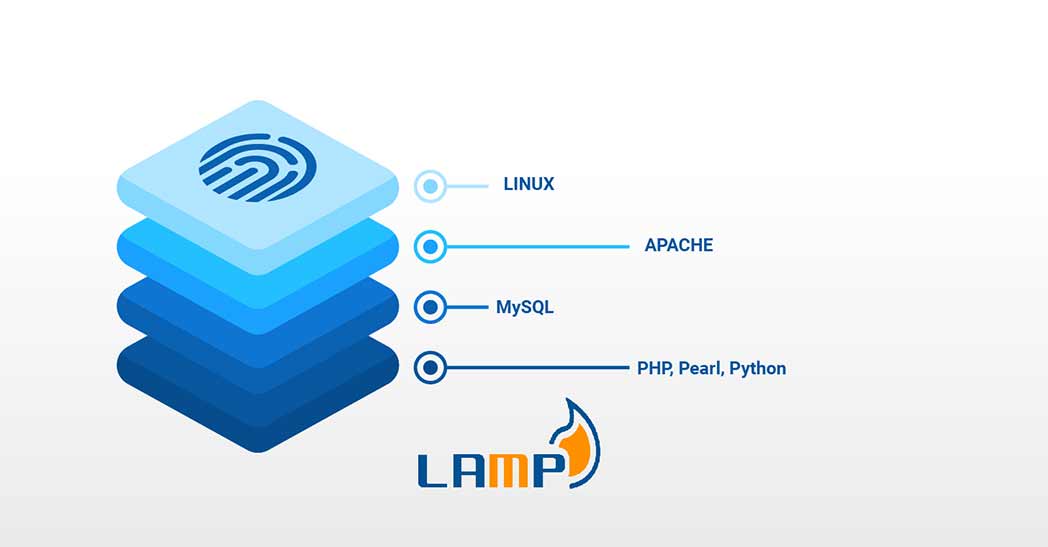
LAMP Stack setup – Linux Apache MySQL PHP
LAMP is an acronym of a very popular web stack – Linux, Apache, MySQL, PHP. All of the four components of LAMP are open-sourced and are suitable to deploy dynamic websites and web applications. In today’s tutorial, I am going to show you how to set up a cloud server with the LAMP stack. LAMP Stack: L – Linux L in …
How to setup MySQL on a server and MySQL basics
In this CloudSigma tutorial, you will learn how to setup MySQL on a server, and the MySQL basics. MySQL is an open-source Relational Database Management System (RDBMS) that helps users store, organize, and manage data. It is very popular and widely used in the IT industry. Creating the machine First, you have to create a machine. You can do that …
Cloudflare Access: Securing Access to Web Applications
In these times of uncertainties, the global trend is to make the working environment more agile and the work tools more portable. Never has been more important than during the COVID19 crisis with the requirement to work remotely from the main corporate office locations. Cloudflare Access replaces traditional corporate VPN clients by putting Cloudflare’s global edge network in front of …
Run your own VPN server under Docker with OpenVPN Access Server
In this tutorial, I will be setting up an Open VPN server under Docker with CloudSigma. With CloudSigma’s cloud locations spread all over the globe, you can create a server in any of them and access the content from there. Creating the machine First, I am creating a machine with the following resources: 20 GHz CPU 16 GB RAM 20 …
How to use vnStat and iftop to monitor data consumption within a VM
In the generation of cloud computing, virtual machines (VMs) have become very common, while the usage of physical machines has started to gradually decrease. In this post, we will introduce the tools, ‘vnStat’ and ‘iftop,’ which we can use to monitor data consumption in a VM. First, I am creating a machine with the following resources: 20 GHz CPU 16 …
Installing Hadoop on a Single Node in Five Simple Steps
Welcome to our guide on installing Hadoop in five simple steps. To start with, the Apache Hadoop software library is a framework that allows for the distributed processing of large data sets across clusters of computers using simple programming models. It is designed to scale up from single servers to thousands of machines, each offering local computation and storage. Rather …
Host your own Git Repositories with GitLab
In this post, I am going to demonstrate the installation of GitLab. With GitLab, we can host our own repositories at a central place with the ease of the Git features. GitLab is the first single application for all stages of the DevOps lifecycle. Only GitLab enables Concurrent DevOps, unlocking organizations from the constraints of the toolchain. In addition, GitLab …
Setting up a Blog Using Ghost
Ghost is a fully open source adaptable platform for building and running modern online publications. With Ghost, setting up a blog is a child’s play. It gets easier with CloudSigma’s already prepared base library OS images. Introduction To start with, I am creating a machine on CloudSigma with 5 GHz CPU and 8 GB RAM. I am naming it “Ghost-Blog” …