A while back I wrote a guest post on BitTorrent’s blog about how to use BitTorrent Sync as an alternative to cloud storage services, such as Dropbox and Box. As a result, this post is an expansion of that post that provides more clear step-by-step instructions on how to securely deploy BitTorrent Sync. Security notes First, since the focus of …
An introduction to server provisioning with CloudInit
This month we announced a very exciting partnership with Canonical, the makers of Ubuntu. Above all, the main element in this partnership is the introduction of full CloudInit support between the CloudSigma cloud and Ubuntu. An introduction to CloudInit If you’re not familiar with CloudInit, it is the industry standard for bootstrapping cloud servers. To clarify, if you are using …
How to run Docker on CloudSigma (with CloudInit)
First, you need to have knowledge of a few pre-requisites: An SSH key. Basic understanding of Docker. The official documentation is a great start. Basic knowledge of CloudInit In the recent year or so, Docker has received a tremendous amount of attention. It appears to be one of those things where the timing was just perfect. While the concept of …
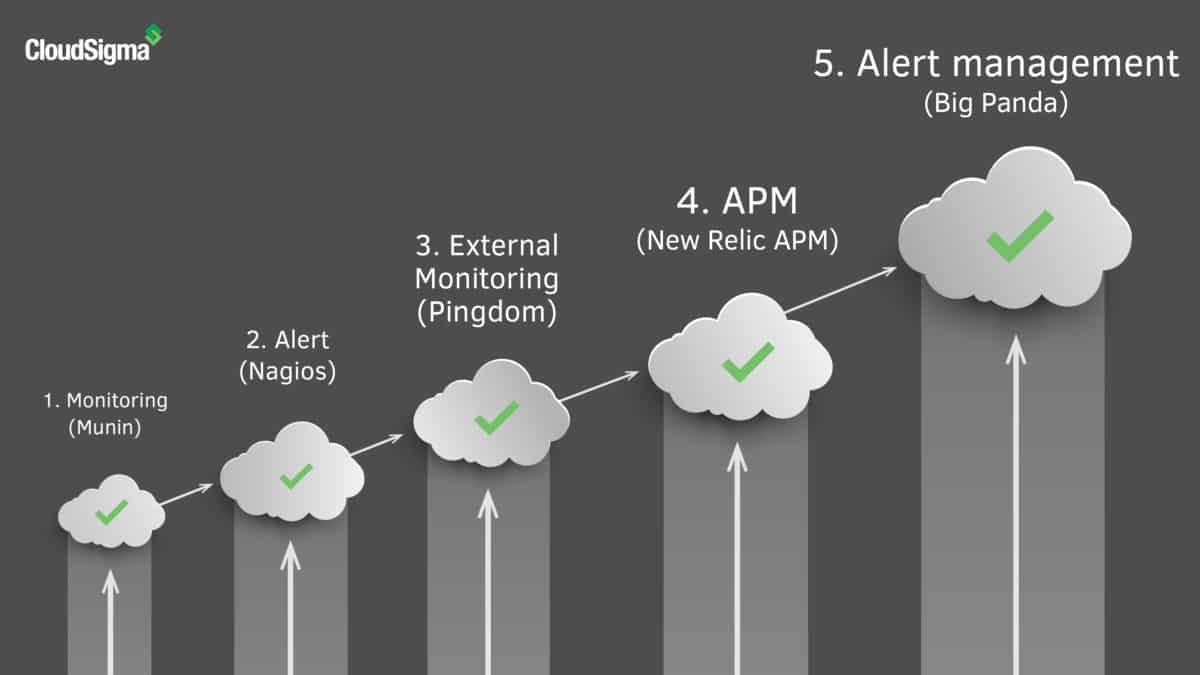
Five Tools You Need for Your Cloud Deployment
You have finally managed to get up and running with your application. It runs great. You’re happy and you’re customers are happy. One morning you wake up with an inbox full of angry customer emails and your Twitter feed full of complaints. While you were sleeping, something broke. You just didn’t know about it until this morning when you checked …
An introduction to failover in the cloud
One of the hardest, but most important things to do when building your cloud architecture, is to eliminate Single Point of Failures (SPoF). What this means is that every mission critical service should be able to survive an outage of any given server. Some companies, like Netflix, have taken this to an extreme and created a service called Chaos Monkey. …
Using Ansible with CloudSigma
In a recent article I wrote about how you can use Salt to manage your CloudSigma infrastructure. However, another tool mentioned in that article was Ansible, which is in many ways similar to Salt. Since we’re all about choice here at CloudSigma, I thought it was only fair to also provide Ansible-users (or aspiring users) with an easy way to …
Build your own PaaS (with Dokku)
One of the most popular PaaS providers today is Heroku. Heroku, along with other PaaS providers like Engine Yard is loved by developers because it makes the deployment of a new application extremely fast and simple. It’s not hard that most developers would rather write code than setting up and troubleshoot servers. So it’s not hard to figure out why …
NTP Amplification Attacks, the latest DDoS weapon (and how to protect yourself from it)
During the last few months, we’ve seen an increased amount of NTP amplification attacks. It’s an attack technique, similar to the previous wave of DNS amplification attacks, mostly used by script kiddies (but also by black hats) to take sites/servers offline. The technique behind of the attack is pretty simple; using public NTP servers, the attacker sends a request and …
Spice up your servers with Salt
In recent times, the automation tool Salt has gained a lot of attention. In fact, Salt, along with Ansible, are seen by many as refreshing alternatives to the more established automation tools Puppet and Chef. Recently, a new tool was added to the Salt stack named salt-ssh, which enables you to manage servers without having to install any tools on …
Running FreeBSD, NetBSD and OpenBSD in the cloud
With our sponsorship of EuroBSDcon 2013, a blog-post on the topic of FreeBSD, NetBSD, and OpenBSD felt in order. If you didn’t already know it, we’re one of the few cloud providers in the world that allows you to run unmodified FreeBSD, NetBSD and OpenBSD (including derivatives, such as pfSense). If you simply want to take one of these systems …
Simplifying maintenance with fabric and pycloudsigma
When you’re working with a cloud infrastructure, it’s pretty common that you need to perform the same task on all your servers. Perhaps you need deploy a hotfix, or simply just check what kernel version your servers are running. The traditional sysadmin way of doing this was to simply write a for-loop in shell-script which fires off the execution of …
Virtual machines and disk expansion
Disclaimer: Before we begin, we need to point out that there is always a risk of data loss when you are doing disk expansion. Hence, you should always back up your data before you begin. We do not assume any responsibility for data loss caused by this guide. It is up to you to take proper backups. One of the …